User Tools
Sidebar
session:mid-ctf
This is an old revision of the document!
Table of Contents
Session 06 - CTF
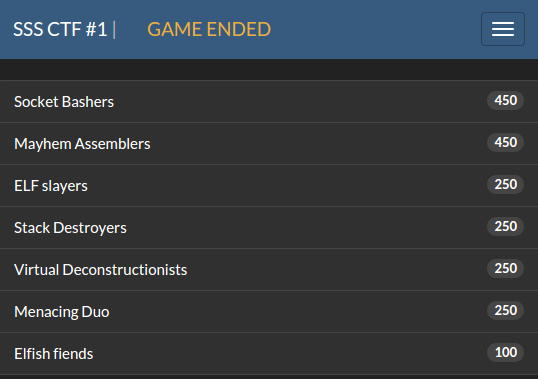
Final Scoreboard
Slides
Tasks
Task archive: ctf1_package.tgz
- For the exploit tasks you need to spawn a shell and obtain the information in
~/flag. - For the reversing task just send the SHA256 hash of the correct password as the flag
Login with the team info and send your flags at http://146.148.57.172:5000/login.
- Task 1: Case Service ⇒ exploit task 100 points
nc 146.148.14.230 1111
- Task 2: HiberCal ⇒ exploit task (source provided) 150 points
nc 130.211.49.27 3333
- Task 3: Case Service Reloaded ⇒ harder exploit, variation on task 1 200 points
nc 146.148.122.41 2222- Please use the following version of the binary caseservice_reload.zip
- Task 4: XeroX ⇒ reversing task 150 points
- Task 5: ElfGrande ⇒ reversing task 150 points
Hints given out:
- Tasks 1 & 3:
- similar to Heartbleed
- passwords are words than can be found in a dictionary
- Tasks 2:
- the stack is not executable (no need for shellcode, we'll be discussing these in a later session)
Discussion
Please use the #hexcellents channel on Freenode. You can use a stand-alone IRC client or a web-based client such as Freenode webchat or KiwiIRC.
session/mid-ctf.1437847645.txt.gz · Last modified: 2015/07/25 21:07 by Vlad Dumitrescu
Except where otherwise noted, content on this wiki is licensed under the following license: CC Attribution-Share Alike 4.0 International